The Easter-weekend slowdown at Adyen, the four-day contactless freeze at Marks & Spencer, and February’s one-hour outage at Square all happened inside the first four months of 2025.
Together, they halted thousands of tills, stranded millions of consumers, and forced senior managers to re-draw their risk maps overnight. The events differed in vector and duration, yet each one translated almost immediately into lost sales, disputed transactions, and bruised brand sentiment, three metrics boards track far more closely than packet drops or CPU load.
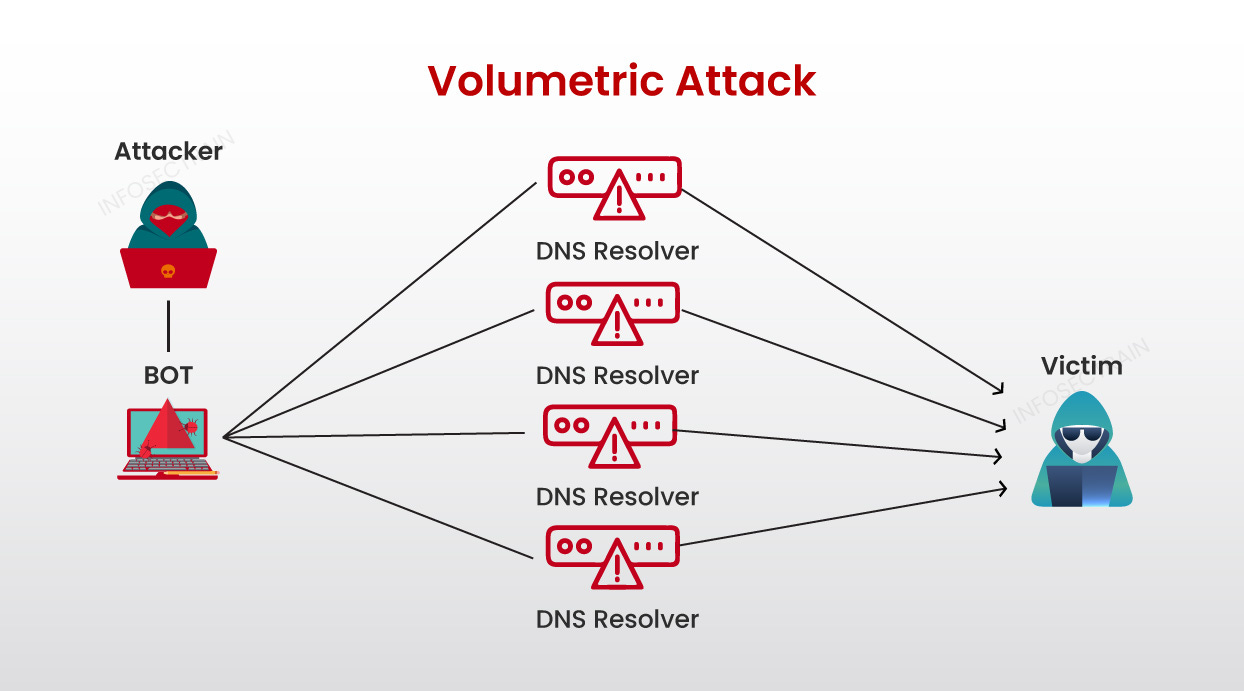
Adyen fought off three high-volume denial-of-service waves that throttled its European edge for about eight hours spread across two days.
Marks & Spencer ran card dips while queues stretched through aisles after an internal containment measure severed its cloud-tokenisation link.
Square, finally, tripped on a routine certificate rotation and discovered that a sixty-three-minute gap in service is plenty of time for social media to fill with screenshots and refunds.
While it might be too early to point to a pattern, what I have noticed in the last few months is that the sophistication of these attacks and technological challenges is increasing, and that even those we deem to be the pinnacle of excellence in our industry are not entirely immune to it.
So in this newsletter, I will break down the trends I am observing and what we in the industry can do about them.
Let’s dive in…
Rising incentives, falling barriers
Let’s start with some facts.
Cybercrime grew into a $16 billion business in the United States alone last year, a 33% jump that eclipses the combined revenues of many regional acquirers.
Cloudflare’s telemetry shows that denial-of-service traffic now accounts for 37% of all web-application attacks, and most of those bursts last less than ten minutes, a window too narrow for manual mitigation.
Imperva’s bot-management census estimates that automated scripts run 37% of the public internet, with credential-stuffing and checkout-abuse among the fastest-growing sub-categories.
On the defender’s side, the talent pool remains chronically thin: Visa’s workforce-analysis white paper counts 3.5 million unfilled cyber roles worldwide and projects continued double-digit vacancy growth through 2027.
Payments operations concentrate several attractions for attackers.
The data payload, primary account numbers, dynamic tokens, and verified identity attributes command premium resale prices. With settlement flows that complete in seconds, intruders can monetise access almost immediately.
Above all, merchants and PSPs run on service-level objectives measured in milliseconds, which means even short-lived disruptions translate directly into revenue leakage and support-desk spikes. A real-time settlement rail cannot revert gracefully to batch mode; it either clears in near-real time or it stops.
Three incidents, three patterns of weakness, explained
So whenever incidents occur, the headlines focus on the result, which is often a loss of revenue, long lines in stores, or websites that can’t process payments, leaving customers complaining online.
While I am no expert, let me try to explain what I found out happened in the three incidents that occurred to Adyen, Marks & Spencer, and Square.
Adyen | 21–22 April, 2025
While Adyen operates as a global processor, the Dutch company funnels its European traffic through two edge clusters before routing it to regional points of presence.
A volumetric denial-of-service attack (meaning the attacker used a bot to send a large volume of traffic to saturate the victim's bandwidth), therefore, choking card acquisition, wallet APIs, and local-scheme routing in one stroke.
While authorisation rates never fell to zero, latency breached merchant timeouts and produced the same commercial outcome as a hard outage.
This exposed how physical diversity at the data-centre layer does not guarantee logical diversity at the edge, in other words, if traffic policy pushes too much load through a single choke-point, attackers need only saturate that point.
Marks & Spencer | 19–24 April, 2025
While Retail analysts speculated about ransomware, the immediate cause of M&S’s disruption was the cure, not the infection. Security teams segmented the internal network to stop lateral movement. The action isolated the cloud token-switch that converts DPANs into PANs for authorisation. Contactless taps failed, online click-and-collect kiosks froze, and older chip-and-PIN flows operated in riskier offline mode.
This showed us that the chain’s experience demonstrates that while merchants adopting cloud tokenisation gain flexibility, they also inherit another critical dependency: the private link between every terminal and a token vault hundreds of kilometres away.
Square / Cash App | 26 February, 2025
Then there is Square’s incident, where a certificate bundle expired ahead of schedule.
Microservices refused mutual TLS (it means that one or more microservices in your system did not accept or establish a connection using mutual TLS (mTLS) authentication), and authentication errors rippled through point-of-sale lanes, VISA Direct payouts, and peer-to-peer transfers.
The total incident lasted just over an hour, but by the time engineers re-deployed the certificates, merchants had queued refunds, and consumers had switched to alternative wallets.
The lesson is evident: every manually managed secret counts as unfinished automation, and unfinished automation is a latent outage.
Across the three cases, no advanced malware strain appeared, and no zero-day exploit hijacked remote code execution.
Either attackers pushed volume against a thin edge, the payments companies themselves pulled the wrong plug under pressure, or simply operators who overlooked a routine maintenance chore.
However, each weakness sits firmly inside the part of cybersecurity budgets labelled “basic hygiene,” yet each has generated headlines and tangible commercial loss.
So, what are payments companies doing to prevent this from happening?
The networks are beefing up their defences in both people and technology.
Visa has been aware of the talent shortage for a while and has already taken steps internally and externally by investing time and energy in training and recruiting thousands of security specialists. They have also added a mandatory Payments Cybersecurity Academy and invested $9 billion in network defences since 2020.
The result is clear: those systems blocked $4.2 billion in attempted fraud last year before authorisation. Visa’s public emphasis on people development is not brand theatre; it reflects a conviction that new firewalls and anomaly models will plateau unless we start investing in people who can help us defend against them.
Mastercard is using a different strategy, expanding outward instead of inward.
In late 2024, it agreed to acquire threat-intelligence house Recorded Future for $2.65 billion. The data produced by that platform feeds directly into card-laundering heuristics and compromised-card discovery, cutting detection lead time by half during pilot projects.
By integrating intelligence into decision engines, Mastercard hopes to move the conversation from perimeter defence to predictive risk scoring, a logical step when attackers iterate campaigns faster than rule writers can review them.
Large PSPs are stress-testing rather than theorising.
Adyen, Stripe, and Worldline now conduct quarterly “chaos days” in which red teams release synthetic floods and credential-stuffing storms into production-mirrored environments. Operations succeed only when checkout latency remains below two hundred milliseconds throughout the assault.
Payments 4.0 Security for the rest of us
Knowing all this, what can we take away from it?
We must understand that cybersecurity now drives revenue as much as it keeps lights on. The best way to think about it is like this:
Speed equals sales. When checkout response slips past 300 ms, carts drop, chargebacks rise, and support calls flood. Instead of using that as another metric, payment companies must add those delayed minutes to their quarterly KPIs so security spending links directly to income.
People before tools. AI dashboards are useless if no engineer investigates the alerts. There is a reason Visa has an in-house cyber academy and Mastercard has purchased Recorded Future, because they understand that a skill gap needs to be addressed.
Reliability wins deals. Merchants already split volume across acquirers for better pricing and approval rates. While we never know where the next attack is coming from, the response from merchants will be that they will steer more traffic to partners they perceive as being steady.
Share the threat data. To think that attackers are lone hackers in an attic is unrealistic. Attackers swap tactics in real time. I am a big proponent of PSPs starting to exchange "(anonymised) incident details to cut detection time for everyone.
Conclusion
As payments traffic keeps climbing, attacks get cheaper, and millions of security roles remain unfilled, payments companies must take cybersecurity more seriously.
By adding latency metrics to product dashboards, recruiting or partnering to help fill the scarcity in expertise, deploying real-time risk models, and joining data-sharing networks.
Treat security as a growth lever today, or pay for it later in refunds and lost volume.
Thank You for Reading. Please like, Comment, Share, or Post on Your Social media. I appreciate all the feedback I can get.
P.S. If you want to work with me in a larger capacity, either speaking, advisory, or consulting, feel free to email or DM me.